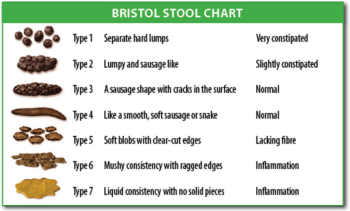
Next time you want to gain some points when talking to the house surgeon you could report your patients' stool characteristics with the professional Bristol Stool scale... Expect at least 3-4 seconds of silence on the line!
November 27, 2011
November 18, 2011
Ask a friend - the universal EM questions experiment
The problem is still that we haven't got so many to ask when our group is exhausted. But that doesn't silence the hunger for an answer, in the opposite the frustration just grows.
 I am sure there are other colleges out there, in dark corners - having exactly the same problem. So I decided to start an experiment to see if we can relief the frustration with modern crowdsourcing. Therefor I have started a Google Docs document, open for everyone to edit, with a few questions from our group to kickstart this project. Michelle Lin (UCSF) has previously had experience with Google docs crowdsourcing and has a huge interest to in EM academics so I asked her to help me and she even has a question on the list, waiting for a clever EM physician to answer.
Should this go well I am prepared to take it a step further and develop a better platform but currently I think Google Docs this is the easiest way to start. Remember if you have a Google account the document will reside as shared on your GD home page and be bolded everytime there is a new question/answer.
I am sure there are other colleges out there, in dark corners - having exactly the same problem. So I decided to start an experiment to see if we can relief the frustration with modern crowdsourcing. Therefor I have started a Google Docs document, open for everyone to edit, with a few questions from our group to kickstart this project. Michelle Lin (UCSF) has previously had experience with Google docs crowdsourcing and has a huge interest to in EM academics so I asked her to help me and she even has a question on the list, waiting for a clever EM physician to answer.
Should this go well I am prepared to take it a step further and develop a better platform but currently I think Google Docs this is the easiest way to start. Remember if you have a Google account the document will reside as shared on your GD home page and be bolded everytime there is a new question/answer.Alright, everything is set and we are ready to go. The magic link then is
https://docs.google.com/document/d/1oDFuaYJrOT5UJolsmgudVfdLSkeYvuTsMkmVpz7d9Ds/edit
ADDENDUM feb 2012
 Judging by Blogger statistics this post has had very many readers so I assume the idea must be something my colleges are interested in. As I had suspected the text based format is not the best one if this is to roll on, for example there is no way to "upvote" a the best answers and just pushing answered questions further down is no good way of archiving old questions.
Judging by Blogger statistics this post has had very many readers so I assume the idea must be something my colleges are interested in. As I had suspected the text based format is not the best one if this is to roll on, for example there is no way to "upvote" a the best answers and just pushing answered questions further down is no good way of archiving old questions.In the meantime I have discovered Quora which seems to fulfill all our needs of an easy, web-based Q & A tool for asking and answering EM questions by the community. Although not locked or restricted, it's tagging and grouping system would make it incredible easy to use for the EP community and being a modern social-web based tool (for example using Facebook login credentials) it has the potential to become the true tool I was looking for. The one thing we need is more EPs to sign up and start using it and as such I suggest you all go there and start following the Emergency medicine group.
November 17, 2011
IT for emergency physicians - the esoteric talk
 In september 2011 I was at the 6th MEMC, an international emergency medicine conference held in the small greek island of Kos - the birthplace of Hippocrates. I was given the opportunity to talk about my IT experiences in my life as an physician.
In september 2011 I was at the 6th MEMC, an international emergency medicine conference held in the small greek island of Kos - the birthplace of Hippocrates. I was given the opportunity to talk about my IT experiences in my life as an physician.The thought of a first first time talk on international ground was comfortably stressful until the day before when I decided a trip to an Irish karaoke-bar would stabilize my nerves. And it did but the irish bartender spotted my Acchiles' heel and managed to sneek more beer on my table than I had planned for, fiddling most of my cortical senses and spinal reflexes the day after.
There was a silent nervous breakdown going on and standing in front of tens of ED docs, masters of spotting obfuscate symptoms, it was a little hard to give "the perfect talk". A faux pas for martians even. Fortunately the content of my talk was of more interest than performance and it seemed the audience forgave me stuttering words with a mixture of esoteric swedish, icelandic, english-wannabe pronunciation. I even had a short-lived crowd gathering afterwards asking for my name tag and email which I like to think was a positive sign.
And now, I give to you a "home edited" version of the same talk, with the same esoteric pronunciation for you only to feel the atmosphere of the real talk...
Keep in mind I was limited to 20 minutes and to dissect a broad topic as IT in such a short time would be utterly impossible. Instead, I give you a few eye-openers and ideas for you to step onto the IT-wagon yourself and I welcome you to follow my blog for the details.
Please feel free to ask any questions you have in the comments and I will happily reply. If you find an urge to discuss with me karaoke as stress-relief therapy, you are welcome to contact me - you will find contact info in the introduction post.
IT for emergency physicians from David Thorisson on Vimeo.
November 8, 2011
8. Online security - preventing your digital catastrophe
I have just read an article about a womans' great misfortune where her Gmail account was not only hacked but all her online data erased. A chilling reminder of how vulnerable we are with our life stored in the cloud; years of correspondance, documents and personal photos. An event like this would leave me stunned for weeks as most if not everything I have created is now online. The article is a must read for everyone, it is not only a wake up call but a lesson learned how to defend your self from modern crimes - being hacked online.
Being both paranoid and proactive I have never in my years of computing had an intrusion, neither at home or online. As IT engaged doctors, defending our online forte is on of our most important tasks. Unlike other physical things that we insure because they can be replaced, the day that you are hacked is the day you can loose it all. Thus I would like to share with you my experience and techniques.
Please remember to also read the article, they are 10 minutes well spent!
I have two Gmail addresses. The primary one I give out only to those I fully trust, thus mainly family and friends. I would even hesitate to give it out to people I am not sure about since if their email accounts are hacked, my address will most probably go to some hacker's database and thus online. The other email I use as my "shield" and I use it for registrations, postlists etc where anything can happen.
Then I use the primary Gmail account to import from the secondary one. Gmail's spam filter has then automatically removed 99% of suspicious emails and even though a few "genuine" emails get caught in the spam filter I don't care since they're not personal anyway.
In the end your email will eventually leak (in my case, my mother's email account got hacked, I never had spam emails until then) but this technique minimizes the visibility of your email. This is why I also use my secondary email for postlists or online orders, even though I trust the companies they just might get hacked one day and the hackers most surely will be looking for gmails to hack!
A very common mistake is that of reusing passwords. You might for example have the same password on your Gmail account as on some general news-site, say your subscription to Wall Street Journal. Hackers know this and therefor put efforts into breaking into the databases of these seemingly non-important sites to catch logins. Someone breaking into my WSJ account is utterly unimportant to me - at most the hacker will be able to read some locked WSJ articles but they will not be threatening my online world in any way. My online bank login on the other hand is a very vulnerable one obviously. With so many online logins to hold account on you need to define which ones are truly vulnerable and take special care of these. For the rest, you can ease your paranoia and reuse your password. This will also make it much easier to hold account of tens of logins as modern IT life requires us to do.
With special care I mean choosing your password wisely, renewing it on regular basis and storing it carefully. There are many nice software solutions for this, I prefer phone based ones since I have my phone always with me and thus easily used for looking up not only web-site passwords but PIN- and door codes. For this I use the highly recommended Android app Pocket - there are iPhone apps for this too.
Your only protection is to be truly paranoid and avoid unsecure WiFis. If you insist, minimise access to your personal sites requiring login.
This is impossible, I know. Fortunately there are less dramatic alternatives - securing browser traffic with https for example (see below) and using VPN (virtual private networks). Until you feel totally sure about your hotspot vulnerabilities I recommend you to use your laptop lightly unless you have access to a secured WiFi, some cafeterias actually do provide their customers with a password for this purpose.
And remember to check your WiFi setup at home - the once trusted WPA protocol is now easily hacked and you should only be using WPA2.
Now this is not something for the average computer user to understand from just one blogpost. Because how truly important this is I highly recommend that you give yourself some time and read more about WiFi security, here is a great website which will cover the basics in an easily read text:
http://www.nowiressecurity.com/about_wi-fi_security.htm
Unfortunately there is no one solution to fight off malware but having a decent anti-virus software will do it for most of these - at the same time clogging your computers' resources (some will take up to 20% of your CPU). This is one of the reasons I am totally converted to Linux - something I will be blogging about in just a few days.
You might have noticed from previous posts my love for Chrome, the fact that Google has offered $20.000 to anyone who claims it can be hacked says all that needs to be said.
Being both paranoid and proactive I have never in my years of computing had an intrusion, neither at home or online. As IT engaged doctors, defending our online forte is on of our most important tasks. Unlike other physical things that we insure because they can be replaced, the day that you are hacked is the day you can loose it all. Thus I would like to share with you my experience and techniques.
Please remember to also read the article, they are 10 minutes well spent!
Protect your email address
A login is a combination of password and email. Thus keeping your primary email away from the Internet is a strong tactic of defense since the hacker has no way of cracking your password.I have two Gmail addresses. The primary one I give out only to those I fully trust, thus mainly family and friends. I would even hesitate to give it out to people I am not sure about since if their email accounts are hacked, my address will most probably go to some hacker's database and thus online. The other email I use as my "shield" and I use it for registrations, postlists etc where anything can happen.
Then I use the primary Gmail account to import from the secondary one. Gmail's spam filter has then automatically removed 99% of suspicious emails and even though a few "genuine" emails get caught in the spam filter I don't care since they're not personal anyway.
In the end your email will eventually leak (in my case, my mother's email account got hacked, I never had spam emails until then) but this technique minimizes the visibility of your email. This is why I also use my secondary email for postlists or online orders, even though I trust the companies they just might get hacked one day and the hackers most surely will be looking for gmails to hack!
Secure your password
Hackers are not guessing your passwords today and trying a few entries until they give up. They have robots which make "brute-force" attacks on your accounts with thousands of words per second, combinations of words caught by spying your online social life (e.g. birthdays and children's names) and a pool of "most common passwords". Not only do you have to choose your password carefully but you should renew if at least every 6 months. The IT friendly site Makeuseof has a nice article on creating a password a little harder to break, if you really want to dwell (highly recommended!) into this subject I can also recommend Lifehacker's articles.A very common mistake is that of reusing passwords. You might for example have the same password on your Gmail account as on some general news-site, say your subscription to Wall Street Journal. Hackers know this and therefor put efforts into breaking into the databases of these seemingly non-important sites to catch logins. Someone breaking into my WSJ account is utterly unimportant to me - at most the hacker will be able to read some locked WSJ articles but they will not be threatening my online world in any way. My online bank login on the other hand is a very vulnerable one obviously. With so many online logins to hold account on you need to define which ones are truly vulnerable and take special care of these. For the rest, you can ease your paranoia and reuse your password. This will also make it much easier to hold account of tens of logins as modern IT life requires us to do.
With special care I mean choosing your password wisely, renewing it on regular basis and storing it carefully. There are many nice software solutions for this, I prefer phone based ones since I have my phone always with me and thus easily used for looking up not only web-site passwords but PIN- and door codes. For this I use the highly recommended Android app Pocket - there are iPhone apps for this too.
Beware unsecure wireless networks
Modern hackers will not only try to pick lock your passwords - another less known method is that of sniffing network traffic to eventually find your password amongst millions of data packets. It may sound difficult but this can be done in just seconds with software easily found on the Internet. Free networks ("hotspots") are available all over, especially in caféterias where you are welcomed to sit down with a nice Cappuccino to browse the Internet and do your work. To save you from the hassle of logins the hotspots commonly offer open WiFis meaning that every single data packet coming to or from your computer is open to the public. If you are like me you most probably have accessed these WiFis with your smartphone, I have to admit I hadn't realised the danger of this until I read the article above.Your only protection is to be truly paranoid and avoid unsecure WiFis. If you insist, minimise access to your personal sites requiring login.
This is impossible, I know. Fortunately there are less dramatic alternatives - securing browser traffic with https for example (see below) and using VPN (virtual private networks). Until you feel totally sure about your hotspot vulnerabilities I recommend you to use your laptop lightly unless you have access to a secured WiFi, some cafeterias actually do provide their customers with a password for this purpose.
And remember to check your WiFi setup at home - the once trusted WPA protocol is now easily hacked and you should only be using WPA2.
Now this is not something for the average computer user to understand from just one blogpost. Because how truly important this is I highly recommend that you give yourself some time and read more about WiFi security, here is a great website which will cover the basics in an easily read text:
http://www.nowiressecurity.com/about_wi-fi_security.htm
Be very afraid of malware
In the early days of PCs you were required physical actions to install software such as inserting a CD. Today the mere click of a link is enough to wreak havoc, unless your computer is well protected (Windows is especially vulnerable). Malware is tiny piece of malicious software - computer virus is one kind of these - built with the purpose of taking over your computer or parts of it for various purposes. The least scary ones just want to use some of your CPU power for a bigger project while the true beasts will record every single keyboard stroke, waiting to catch your passwords or credit card numbers. What is most frightening with malware is that they will commonly install themselves without you noticing anything, sitting in the background waiting for you to fall to it's mischiefs, like a spider in it's net.Unfortunately there is no one solution to fight off malware but having a decent anti-virus software will do it for most of these - at the same time clogging your computers' resources (some will take up to 20% of your CPU). This is one of the reasons I am totally converted to Linux - something I will be blogging about in just a few days.
Pick your browser
Internet Explorer used to dominate the world of browsing thus becoming a popular target for hackers. A depressive fact considering so much of your work goes through this wonderful technology. But then, IE simply is awful when it comes to security and has caused many days of embarrassment at the offices of Microsoft. Yet another reason to switch to other browsers not only more secure but in every aspect better than IE.You might have noticed from previous posts my love for Chrome, the fact that Google has offered $20.000 to anyone who claims it can be hacked says all that needs to be said.
Special tips for your Google cloud data
The article told about an unfortunate Gmail user and being a very active G user my self I want to emphasize a few points which will dramatically reduce the risk of you being hacked, in addition to those above.- Set Gmail to use https, secure connection. This is your last forte e if you insist on using unsafe hotspots (see above).
- Activate Gmail's 2-step verification; this will disarm anyone who is even making an attempt to hack your account with the little cost of occasional verification codes.
- Activate the recovery options in case you loose your password, it will give you more confidence while picking a truly uncrackable password.
- Beware suspicious links in emails! Although Gmail's spam filter is doing a hell of a good job, an occasional email will slip through and commonly they seduce you to click a link. Which could be the beginning of your worst day of life. Be informed and you won't run into this trap.
- The spam filter works so well because it's crowdsourced - Gmail users report fraud email and the servers will automatically act when a particular email is being repeatedly reported. So it is important that you as well flag mail that you consider fraud, this is easily done with the "report spam" button.
- A backup of your cloud data on Google's servers will give you the ultimate feeling of comfort and good nights' sleep. Here is a great article on this subject and fyi there are rumours about a Google "Gdrive" coming with function simliar to Dropbox. Which would mean automatic backup of everything in Google docs - and maybe more.
See also
- Kill the Password: Why a String of Characters Can’t Protect Us Anymore
"This summer, hackers destroyed my entire digital life in the span of an hour"
November 5, 2011
Cardiology updates 2011 is out!
The world of podcasts is a truly inspiring one, especially in emergency medicine where it seems there is more ambition and spirit of 'sharing knowledge with the rest of the world' than in any other field I know. Although I regularly encounter great lectures this way I decided my blog is not the right place to shout these aloud.
I will make an occasional exception and this time it's Amal Mattu's "cardiology updates 2011", an annual podcast where he reviews the most important literature of the year. It was through these exactly that I caught the podcast train a few years ago and so I see a very good reason to let you know that the 2011 lecture is out.
Put everything else aside, this is the best thing that could happen to you this week. Thanks Amal Mattu and Joe Lex for putting this online. This kind of knowledge truly does lead to better patient care!
http://freeemergencytalks.net/?p=6241
I will make an occasional exception and this time it's Amal Mattu's "cardiology updates 2011", an annual podcast where he reviews the most important literature of the year. It was through these exactly that I caught the podcast train a few years ago and so I see a very good reason to let you know that the 2011 lecture is out.
Put everything else aside, this is the best thing that could happen to you this week. Thanks Amal Mattu and Joe Lex for putting this online. This kind of knowledge truly does lead to better patient care!
http://freeemergencytalks.net/?p=6241
Subscribe to:
Posts (Atom)